Artezio analyzed software and settings for protection of mobile devices from hacking and data theft
Nowadays we became almost inseparable from mobile devices, so I assume your readers would be interested in some simple ways of keeping their personal data safe.
Artezio analyzed software and settings for protection of mobile devices from hacking and data theft.
Please, find the article below and let me know if it suits you for publishing.
Maybe there are others tech-related topics that are interesting for you? I would be happy to share Artezio expertise. Looking forward to hearing from you!
Artezio analyzed software and settings for protection of mobile devices from hacking and data theft
The specialists took into account technical capabilities for protection integrated into the operating systems of mobile devices and selected apps that allowed for an additional level of protection.
In total, 27 apps for mobile devices and personal computers were analyzed.
The experts evaluated the apps based on 14 criteria, among which were the key data protection criteria – the ability to remotely control the device in case of its theft or loss, delete information, lock the screen, notify of unauthorized actions with a device or data.
The top recommended programs includes only four apps that really increase security, all the rest are excluded from testing.
As a result, it was proved that the use of a list of recommendations and selected programs could significantly increase the security of devices running iOS, Android, MAC, Windows, and Linux operating systems.
According to the test results, the following apps are able to provide additional protection:
- Prey
- Hidden
- Cerberus
- Lookout
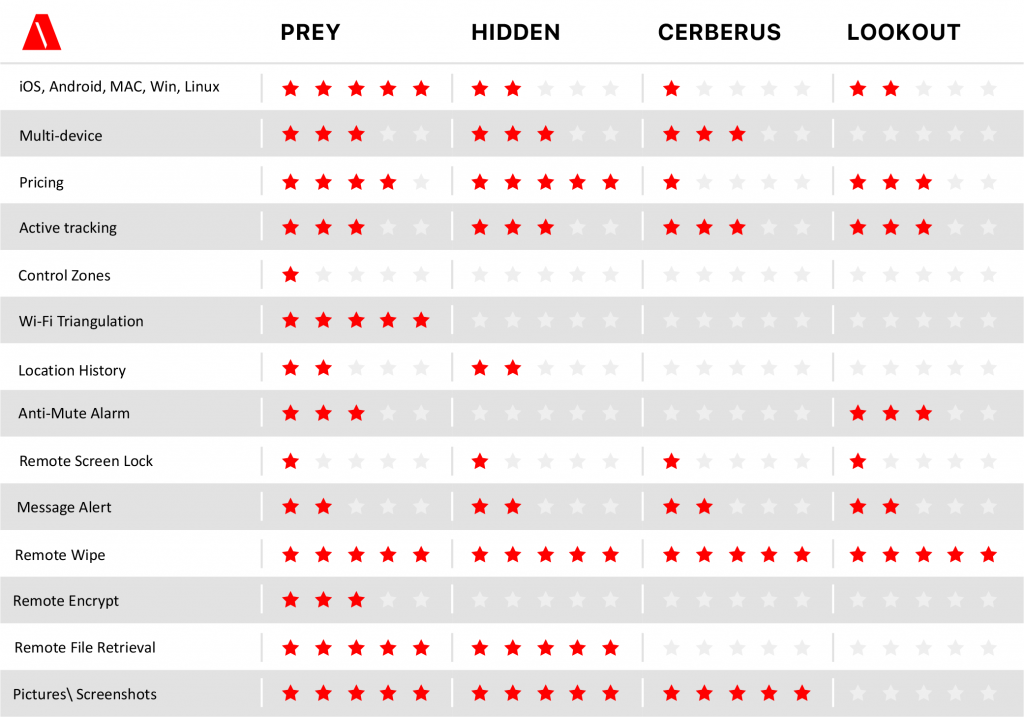
Prey app is significantly ahead of the competition and meets the largest number of criteria, including support for multiple devices and cost of use. A free version of the product is also available for users. The final recommended top list of settings and apps looks as follows:
- Scan the system using the malware search service. It can be done before the antivirus installation.
- Install any antivirus on your mobile device.
- Make sure to create a password or pin to unlock the device.
- Do not use fingerprint or face and eye recognition technologies on devices that have compromised themselves. Pay attention to professional reviews.
- Activate Google Find My Device or Find My iPhone. They are free.
- Delete apps that are installed from unofficial sources.
- Install any app from the list: Prey, Hidden, Cerberus, Lookout.
- Back up information.
- Use special apps to create secret folders with a dual identification or encryption system for additional protection of certain data.
- Do not store sensitive data in cloud services. Accessing a device is much more difficult than accessing a cloud-based data warehouse.
- Do not use SMS for private correspondence, it is better to choose a messenger that encrypts all messages.
- Ensure anonymity in location and negotiations by removing a battery from a mobile device.
- Do not use a standard browser to surf the Internet.
- Use programs that remove metadata from photos and videos you share. This data contains geographic coordinates and a description of your mobile device.
- Disable Wi-Fi, Bluetooth and NFC if you are not using them. There are programs that track and identify device owners by Wi-Fi and Bluetooth.

